Layer 8 Hacking - Linking the OSI Model with the NIST Triangle
By A Mystery Man Writer
Last updated 20 Sept 2024

Layer 8 Hacking - Linking the OSI Model with the NIST Triangle
Layer 8 Hacking - Linking the OSI Model with the NIST Triangle
Layer 8 Hacking - Linking the OSI Model with the NIST Triangle
Layer 8 Hacking - Linking the OSI Model with the NIST Triangle
Recommended for you
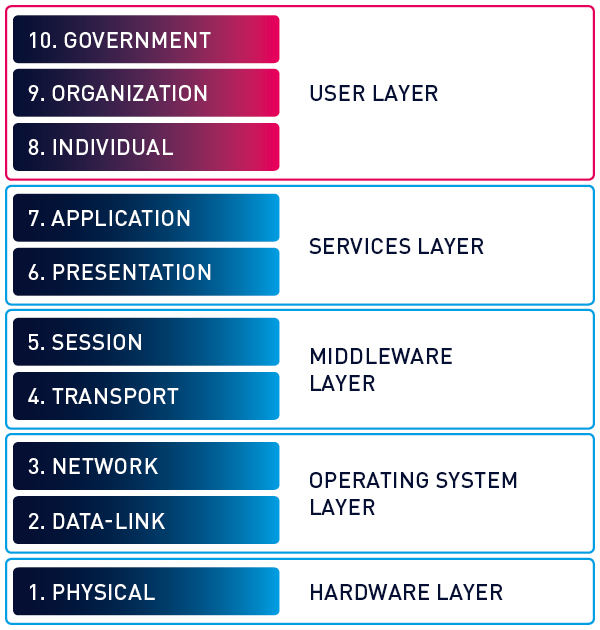 Is It Possible to Monitor OSI Model Layer 8?14 Jul 2023
Is It Possible to Monitor OSI Model Layer 8?14 Jul 2023- Layer 8 Solutions14 Jul 2023
 What is an 8-Layer PCB Stackup? - PCB Directory14 Jul 2023
What is an 8-Layer PCB Stackup? - PCB Directory14 Jul 2023- 8 Layer PCB Manufacturer– Everything You Need to Know14 Jul 2023
- Layer 8 - Soluções em Conectividade - Consultoria e Serviços de14 Jul 2023
 Home - Layer8 Consulting, Inc.14 Jul 2023
Home - Layer8 Consulting, Inc.14 Jul 2023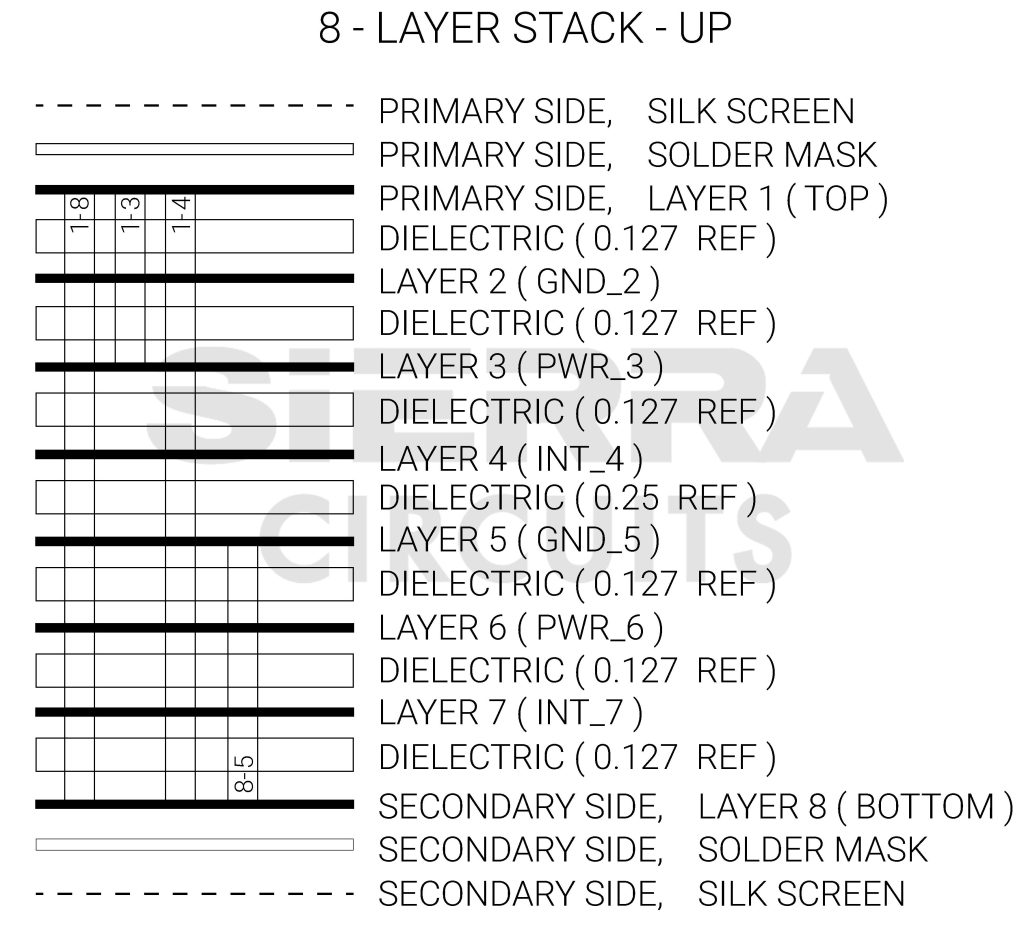 Case study: 8 and 14-layer HDI with Stacked Vias14 Jul 2023
Case study: 8 and 14-layer HDI with Stacked Vias14 Jul 2023 Stackup for 4, 6, 8,, 18 layers Multi-layer laminated structure14 Jul 2023
Stackup for 4, 6, 8,, 18 layers Multi-layer laminated structure14 Jul 2023 Layer 814 Jul 2023
Layer 814 Jul 2023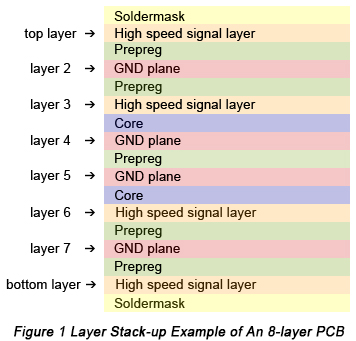 PCB Layer Stackup, PCB Stackup Design14 Jul 2023
PCB Layer Stackup, PCB Stackup Design14 Jul 2023
You may also like
 Reebok Footwear Men NANO X4 Training Shoes BLACK/BOLCYA/LASPIN14 Jul 2023
Reebok Footwear Men NANO X4 Training Shoes BLACK/BOLCYA/LASPIN14 Jul 2023 Elegant Cream White High Waisted Pants14 Jul 2023
Elegant Cream White High Waisted Pants14 Jul 2023 Lemon Yellow - Series 1 - Art Spectrum14 Jul 2023
Lemon Yellow - Series 1 - Art Spectrum14 Jul 2023 Running Tights14 Jul 2023
Running Tights14 Jul 2023 701 Sumner STREET, Esterhazy, SK S0A 0X0 House For Sale, RE/MAX14 Jul 2023
701 Sumner STREET, Esterhazy, SK S0A 0X0 House For Sale, RE/MAX14 Jul 2023 Discover the Ultimate Sports Bra for Women- Boost Your Performance Now – Linions14 Jul 2023
Discover the Ultimate Sports Bra for Women- Boost Your Performance Now – Linions14 Jul 2023 FINAL SALE: Ultra-Soft Modern Jogger - Black – Brooklyn Tailors14 Jul 2023
FINAL SALE: Ultra-Soft Modern Jogger - Black – Brooklyn Tailors14 Jul 2023 Nike Air Max 1 Original Mesh Grey 'Mini Swoosh' ('99).14 Jul 2023
Nike Air Max 1 Original Mesh Grey 'Mini Swoosh' ('99).14 Jul 2023- Women's - Sport Bras or Short Sleeves or Long Sleeves in White or14 Jul 2023
 Buy Black Blazer And Pant Set With Cutdana Work Kalki Fashion India14 Jul 2023
Buy Black Blazer And Pant Set With Cutdana Work Kalki Fashion India14 Jul 2023






